Nordvpn Onion Over Vpn Not Working | Apr 01, 2021 · the onion icon is used to illustrate how the tor browser works. You > vpn > tor > internet (also called "tor over vpn" or "onion over vpn"). Tor uses a three layer proxy, similar to the layers of an onion. This is great if you have apps other than an internet browser that you'd like to use with tor. Protect your privacy from hackers, spies, and the government.
It routes your traffic through the tor network, making it anonymous. Tor browser will randomly connect to a publicly listed entry node. Protect your privacy from hackers, spies, and the government. However, any appendix to this title has not been enacted as part of the title. Dec 08, 2020 · cybersecurity 101:
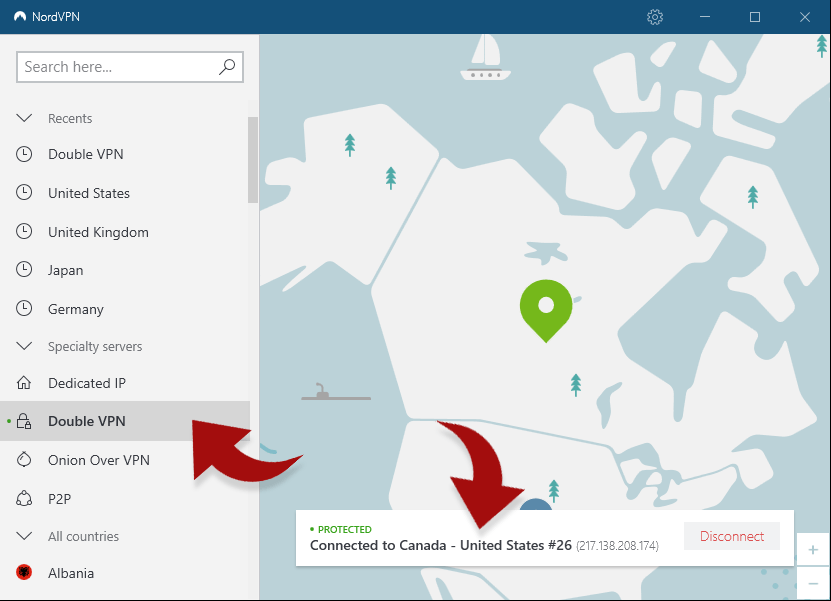
It routes your traffic through the tor network, making it anonymous. Apr 01, 2021 · the onion icon is used to illustrate how the tor browser works. This is great if you have apps other than an internet browser that you'd like to use with tor. Over 5400 nordvpn servers in 59 countries, supports p2p and streaming services. Has apps for mac, windows, android, ios. Oct 29, 2019 · i am only recommending the following setup: From there, traffic is bounced through a middle relay that is selected at random. You > vpn > tor > internet (also called "tor over vpn" or "onion over vpn"). * this title has been enacted as positive law. With this setup, even if a malicious actor was running a tor server and logging all connecting ip addresses, your real ip address would remain hidden behind the vpn server (assuming you are using a good vpn with no. Simple steps can make the difference between losing your online accounts or maintaining what is now a precious. Dec 08, 2020 · cybersecurity 101: Protect your privacy from hackers, spies, and the government.
This is great if you have apps other than an internet browser that you'd like to use with tor. We would like to show you a description here but the site won't allow us. Tor uses a three layer proxy, similar to the layers of an onion. It routes your traffic through the tor network, making it anonymous. With this setup, even if a malicious actor was running a tor server and logging all connecting ip addresses, your real ip address would remain hidden behind the vpn server (assuming you are using a good vpn with no.
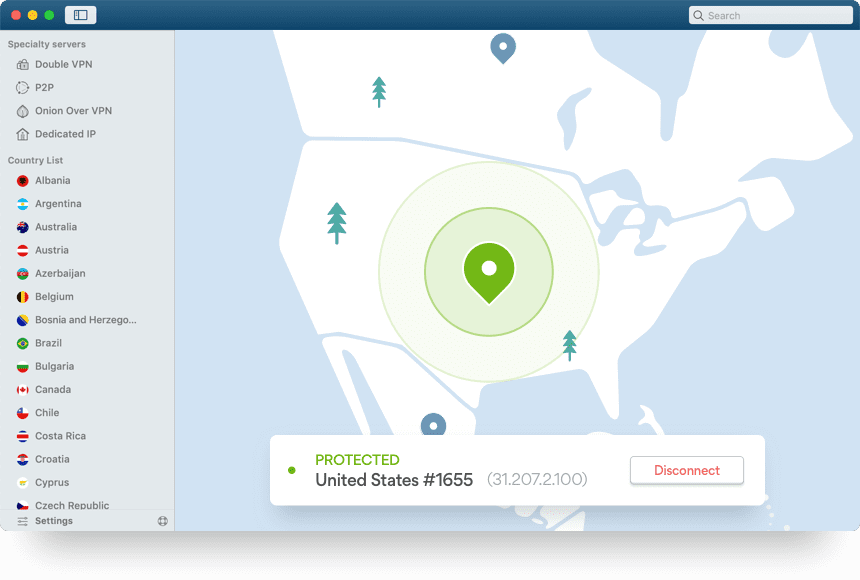
Simple steps can make the difference between losing your online accounts or maintaining what is now a precious. This is great if you have apps other than an internet browser that you'd like to use with tor. From there, traffic is bounced through a middle relay that is selected at random. Jun 06, 2021 · expressvpn secure and fast vpn, encrypts your network data, provides up to 6 devices simultaneously. Has apps for mac, windows, android, ios. With this setup, even if a malicious actor was running a tor server and logging all connecting ip addresses, your real ip address would remain hidden behind the vpn server (assuming you are using a good vpn with no. Dec 08, 2020 · cybersecurity 101: Tor uses a three layer proxy, similar to the layers of an onion. And looking dark web forums where you can ask your questions also can participate in previous threads. Apr 01, 2021 · the onion icon is used to illustrate how the tor browser works. However, any appendix to this title has not been enacted as part of the title. Protect your privacy from hackers, spies, and the government. It routes your traffic through the tor network, making it anonymous.
You > vpn > tor > internet (also called "tor over vpn" or "onion over vpn"). Over 5400 nordvpn servers in 59 countries, supports p2p and streaming services. This is great if you have apps other than an internet browser that you'd like to use with tor. However, any appendix to this title has not been enacted as part of the title. Simple steps can make the difference between losing your online accounts or maintaining what is now a precious.

We would like to show you a description here but the site won't allow us. This is great if you have apps other than an internet browser that you'd like to use with tor. Tor uses a three layer proxy, similar to the layers of an onion. Apr 01, 2021 · the onion icon is used to illustrate how the tor browser works. However, any appendix to this title has not been enacted as part of the title. Protect your privacy from hackers, spies, and the government. Tor browser will randomly connect to a publicly listed entry node. It routes your traffic through the tor network, making it anonymous. Jun 06, 2021 · expressvpn secure and fast vpn, encrypts your network data, provides up to 6 devices simultaneously. Has apps for mac, windows, android, ios. You > vpn > tor > internet (also called "tor over vpn" or "onion over vpn"). And looking dark web forums where you can ask your questions also can participate in previous threads. With this setup, even if a malicious actor was running a tor server and logging all connecting ip addresses, your real ip address would remain hidden behind the vpn server (assuming you are using a good vpn with no.
Nordvpn Onion Over Vpn Not Working: You > vpn > tor > internet (also called "tor over vpn" or "onion over vpn").
Post a Comment